Newsletters often contain links with embedded tracking information. For example, the NY Times Smarter Living Column on the February 15, 2021 had hyperlinked the phrase “isn’t really a recovery for everyone”.
Hovering over that link you find a 442 character long URL: https://nl.nytimes.com/f/newsletter/5qBdGic3TpA1-b-Lby4rIA~~/AAAAAQA~/RgRiDPWSP0TeaHR0cHM6Ly93d3cubnl0aW1lcy5jb20vMjAyMS8wMS8wMS91cHNob3Qvd2h5LW1hcmtldHMtYm9vbWVkLTIwMjAuaHRtbD9jYW1wYWlnbl9pZD0zMyZlbWM9ZWRpdF9zbF8yMDIxMDIxNSZpbnN0YW5jZV9pZD0yNzEzMiZubD1zbWFydGVyLWxpdmluZyZyZWdpX2lkPTg1MDA2ODU1JnNlZ21lbnRfaWQ9NTE2OTAmdGU9MSZ1c2VyX2lkPTg1ODQ4NTNlMGFiYTQwY2UwYmFlYWRlMmIxMjU3ZWJlVwNueXRCCmAhknAqYI81MsBSF2tpbmdmaXNoZXI0MjlAZ21haWwuY29tWAQAAAAA
Following that URL in Postman results in a HTTP 301 (permanent) redirect to another very long URL:
That link in turn results in a HTTP 302 (temporary) redirect to the actual content.
Although the Smarter Living Column (and the New York Times) is a trusted source you could imagine other lets obviously trustworthy sites potentially embedding objectionable content in a long URL – possibly encoded using a service like bit.ly or tinyurl.com. For example, this same NY Times story can be found at https://tinyurl.com/kn4n48er and there are no clues that it is safe or not. In short (no pun intended), other than the domain name, there is little to give the consumer confidence in what content they are about to receive aligns with its stated purpose. (I appreciate this is a contrived problem as the base URL *is* a trustworthy source.)
Chrome Extension
To gain experience working with Chromium extensions I built a small tool to preview encoded URLs as described previously. Starting with a very simple but effective hello-world tutorial – linked here, I built a more complex application called URL Decoder. When the user right clicks on an embedded hyperlink, then left clicks a dialog appears displays the decoded URL. There is also a browser icon where users can manually input URLs to be decoded. The architecture is shown below.
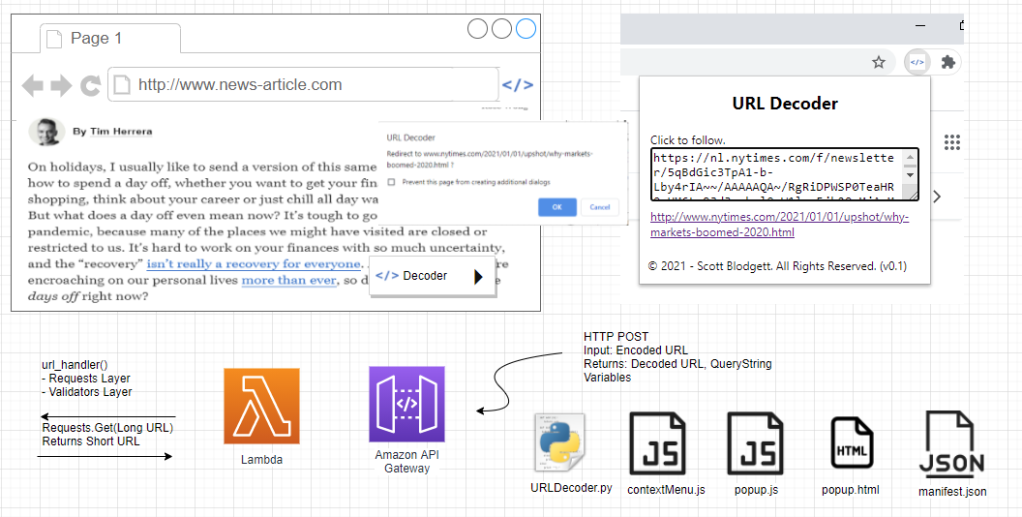
JavaScript inside of the Chrome extension calls an API gateway function via HTTP POST. The API Gateway is the front-end to a Python Lambda function that uses the requests module to retrieve content from the final (re-directed) URL. Noted that the Lambda function is required because (I believe) JavaScript is incapable of making this call due to browser CORS limitations. (“For security reasons, browsers restrict cross-origin HTTP requests initiated from scripts.” Reference link.) Also, the popup is a JavaScript Confirm box which is not capable of being skinned. I believe it may be possible to inject a frame to the page and apply CSS, however, that was beyond the scope of this project.
Flaws
This solution works perfectly if the embedded link uses HTTP 3XX redirects. In practice I found that some (savvy) marketers do not use this technique. For example, this 944 character URL from AWS https://nam11.safelinks.protection.outlook.com/?url=https%3A%2F%2Femail.awscloud.com%2Fdc%2FsRhgdM26bquWWERQj_H99hybECKn_ekLAZUi3uLHL6oMj3xvkM9hJ4eBqy6-VQgems_ssMJHfAcBrHmY89UaFkpDPoyo3FfD7pJTtJH_r-YYsooBlnvOuOTrzg18iFFbC1FVWqzAIeKXEyoFfBvTCQVxatvZT2fuk7fgg9Xb3NlTkVPS91-JGHof9Wrc0tRU_IvGeBy2C98dDcmJF1CD9c7-RU2-tvCIBibtjPGuUZdQPSREStKZapj3i-wl1WtG_hs0AUpdPkoPD07jScUk-VkDMduisUtUDU5UyTVd_KkGr4fx9WtlsuzEzKv_xz0VWkrTJP3TKM5V97kzi8aQiM9sVp5Mkxip0ck6zqqS6DSR6j2s-PkZefqGRyhSkzomYIWiFK-7r94kCoNOPrhYVGv049vWrc5bG2Md9VY4pl35FkQ4L42TJnAs3M08VSUm%2FMTEyLVRaTS03NjYAAAF71UYfzLh1Fbc_CJvuB-7Mda5H9zWnny3Ye-AZt3DaP3xYpvU1qQxiz64FUkL92GfAT3shIY4%3D&data=04%7C01%7CScott.Blodgett%40ctca-hope.com%7C745c5ad585ee45a2c9e208d8e7bf3543%7C9b45049cb0db452f9f3375b120b51c52%7C0%7C0%7C637514155738492229%7CUnknown%7CTWFpbGZsb3d8eyJWIjoiMC4wLjAwMDAiLCJQIjoiV2luMzIiLCJBTiI6Ik1haWwiLCJXVCI6Mn0%3D%7C1000&sdata=eFxgzk1BlZWSrSpzmGdUULPR94TenVFLxQAfDEeTWEk%3D&reserved=0
Results in a 302 which then redirects to an HTML page with a JavaScript redirect to the actual page which can be found at: https://pages.awscloud.com/NAMER-field-OE-AWS-Online-Exec-Focus-March-2021-reg-event.html?sc_channel=em&sc_campaign=NAMER_field_WEBINAR_aws-online-exec-focus_20210330_7014z000001MPSS&sc_publisher=aws&sc_medium=em_60205&sc_content=event_ev_field&sc_country=us&sc_geo=namer&sc_outcome=event&trk=em_60205&mkt_tok=MTEyLVRaTS03NjYAAAF71UYfzDa9N7uc5ng4Icuunx0G1ILXYMYh8bunEE6ZPSKAYkyjidRRZ6q8F1tfJ489YEXjYiPH78z2pUuMNPGskbaXq1UOP0bD1Dk0cjj9DCA7S3nqbYrH

In this case the first redirect works fine, however, the landing page contains a content-less HTML document shell with a JavaScript redirect to the final content. To get around this problem more sophisticated logic would be required which is beyond the scope of this project.
Extension source code is available here on Github.